Leader Election Algorithm In Distributed Systems – Bully Election Leader Algorithm.
Leader Election Algorithm In Distributed Systems Bully Election Leader Algorithm Distributed Computing Bully Algorithm Election Algorithm And Distributed Processing. Leader Election Algorithms in Distributed Systems Election Algorithm in Distributed System Bully Leader Election Algorithm Enhanced Bully Algorithm for Leader Node Election.
Contents
- 0.1 Bully Election Algorithm in Distributed Systems
- 0.2 How Bully Election Algorithm Works
- 0.3 Steps of the Bully Algorithm
- 0.4 Example Scenario
- 0.5 Advantages of the Bully Algorithm
- 0.6 Disadvantages
- 0.7 Code Implementation in Python
- 0.8 Conclusion
- 0.9 Lecture 14: March 21 14.1 Overview 14.2 Leader Election
- 0.10 Lecture 2: Leader election algorithms.
- 1 Why Use Leader Election?
- 2 Bully Algorithm Overview
- 3 Steps of the Bully Algorithm
- 4 Message Types
- 5 Example
- 6 Pros and Cons
- 7 Pseudocode (Simplified)
- 8 Variants
Bully Election Algorithm in Distributed Systems
The Bully Election Algorithm is a leader election algorithm used in distributed systems where multiple processes (nodes) need to agree on a single process as their leader. This algorithm is designed for synchronous systems where processes can communicate with each other reliably.
How Bully Election Algorithm Works
The Bully Algorithm operates under the assumption that:
- Each process in the system has a unique ID.
- Processes communicate using message passing.
- Any process can initiate an election if it detects that the current leader has failed.
- The process with the highest ID becomes the leader.
Steps of the Bully Algorithm
-
Election Triggering:
- If a process detects that the leader has failed (no response), it starts an election.
- The process sends “Election” messages to all processes with higher IDs.
-
Responses from Higher Processes:
- If a higher-ID process is alive, it replies with an “OK” message, indicating it is still active.
- The initiator stops its election, as a higher process will handle the election.
-
If No Response:
- If no higher-ID processes respond, the initiator declares itself as the leader.
- It sends a “Coordinator” message to all lower-ID processes, informing them of its leadership.
-
Election by Higher Process:
- If a higher-ID process is available, it initiates its own election, following the same steps.
- This continues until the highest-ID process becomes the leader.
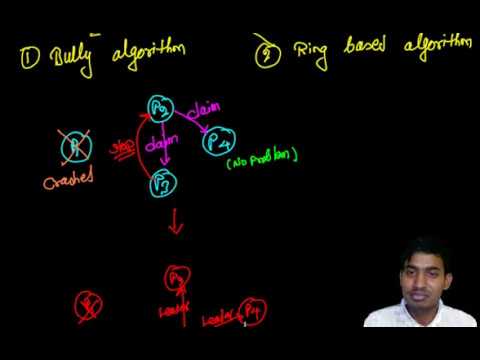
Example Scenario
Assume we have 5 processes in a distributed system with IDs:
P1, P2, P3, P4, P5 (P5 has the highest ID).
- P3 detects the leader (P5) has failed.
- P3 starts an election and sends an “Election” message to P4 and P5.
- P5 is down, but P4 replies with an “OK” message.
- P4 starts its own election, sending an “Election” message to P5.
- P5 is down, so P4 declares itself as the new leader.
- P4 sends a “Coordinator” message to P1, P2, and P3, informing them.
Advantages of the Bully Algorithm
Ensures the highest-ID process becomes the leader.
Works efficiently in failure-prone environments.
Simple to implement in synchronous systems.
Disadvantages
High message overhead (many messages exchanged).
Can cause network congestion in large systems.
Not suitable for asynchronous systems (timeouts may cause false election triggers).
Code Implementation in Python
Here’s a simple implementation of the Bully Algorithm in Python:
Conclusion
The Bully Election Algorithm is widely used in distributed computing to ensure there is a single leader in a system. However, due to its high message complexity, alternatives like the Ring Election Algorithm or Paxos are sometimes preferred in large-scale systems.
Would you like an explanation of an alternative leader election algorithm?
Leader Election Algorithm In Distributed Systems – Bully Election Leader Algorithm
Lecture 14: March 21 14.1 Overview 14.2 Leader Election
Lecture 2: Leader election algorithms.
The Bully Algorithm is a classic leader election algorithm used in distributed systems where nodes (processes) need to elect a coordinator (leader). It is especially useful in synchronous systems where all nodes know each other’s process IDs (or priorities).
In distributed systems, one node often acts as the coordinator to manage shared resources or control system-wide decisions. When the coordinator fails, the system must elect a new leader.
-
Each process has a unique ID (PID).
-
The process with the highest PID becomes the coordinator.
-
Any process can initiate the election if it detects that the coordinator is not responding.
-
All processes know the PIDs of other processes.
-
PIDs are unique and comparable.
-
A failed process may restart and rejoin the system.
-
Reliable communication (message delivery is guaranteed).
Step 1: Election Trigger
If a process notices the coordinator has failed, it initiates an election by sending an ELECTION message to all processes with higher PIDs.
Step 2: Responses from Higher Processes
-
If no higher process responds, the initiator becomes the coordinator and sends a
COORDINATORmessage to all. -
If one or more higher processes respond with
OK, they take over and start their own elections.
Step 3: Final Outcome
Eventually, the process with the highest PID wins and sends a COORDINATOR message to all processes.
| Message | Meaning |
|---|---|
ELECTION |
Sent to higher PID processes |
OK |
Acknowledge, “I’m alive and will elect” |
COORDINATOR |
Announcement of new leader |
Let’s say we have 5 processes:
-
If P3 detects P5 (the current leader) has crashed:
-
P3 sends
ELECTIONto P4 and P5. -
P4 responds with
OKand initiates its own election. -
P4 sends
ELECTIONto P5 (no response), becomes the new coordinator. -
P4 sends
COORDINATORto all.
-
-
Simple to implement.
-
Guarantees that the highest-ID active process is the leader.
-
Generates a lot of messages, especially if many nodes are alive.
-
Not ideal for large or asynchronous systems.
-
Ring Algorithm (less message overhead in large systems)
-
Chang and Roberts Algorithm (improvement on ring-based election)
Would you like:
-
A flowchart of the Bully Algorithm?
-
Sample code implementation in Python?
-
Animation or simulation of how it works?
Let me know how you’d like to learn it further.